
The World’s Best Backup And Recovery
Acronis Cyber Protect Cloud unites backup and next-generation, AI-based anti-malware, antivirus, and endpoint protection management in one solution.

ENHANCE YOUR CYBERSECURITY SERVICES WITH ADVANCED ENDPOINT PROTECTION
Acronis Cyber Protect Cloud unites backup and next-generation, AI-based anti-malware, antivirus, and endpoint protection management in one solution. Integration and automation provide unmatched ease for service providers — reducing complexity while increasing productivity and decreasing operating costs.
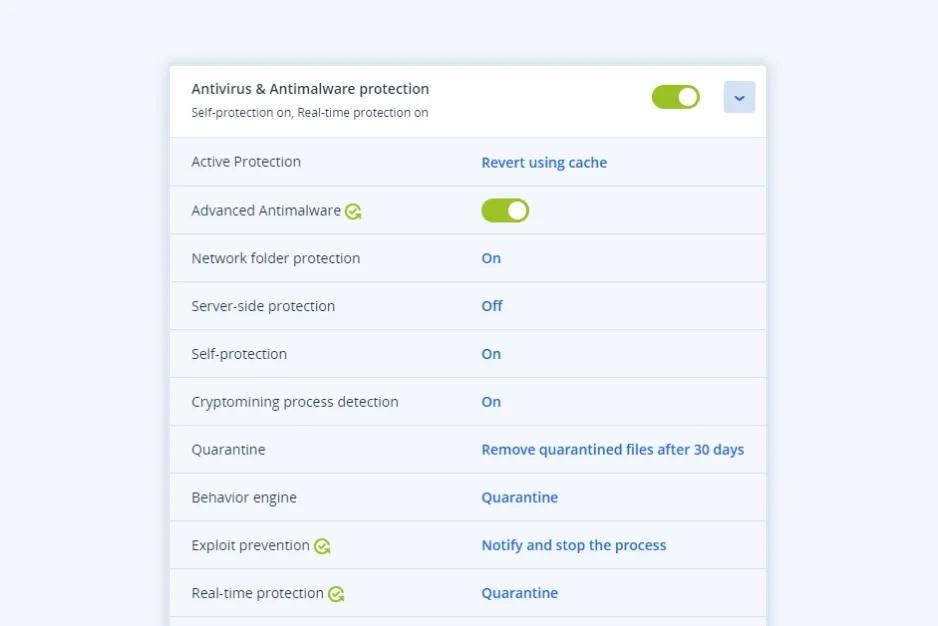
Improve your efficiency to save time and resources
Modernize your endpoint protection by replacing non-integrated antivirus with a single, integrated solution for thorough cyber protection. Accelerate your detection speed, eliminate false positives, and reduce the load by scanning workloads for malware in the Acronis Cloud.
Enable complete, fast, and cost-effective remediation
Protect the recovery process to prevent threat recurrence. Ensure breaches are fully remediated with forensic insights. Ease the process and reduce the cost of security investigations by collecting digital evidence and forensic data in backups, where it’s protected against threats.


CLOUD BACKUP ENHANCED WITH CYBER PROTECTION
Acronis delivers a unique approach by combining cloud backup with cyber protection features, such as anti-malware and antivirus – helping you keep your data secure with more than 20 workload types.
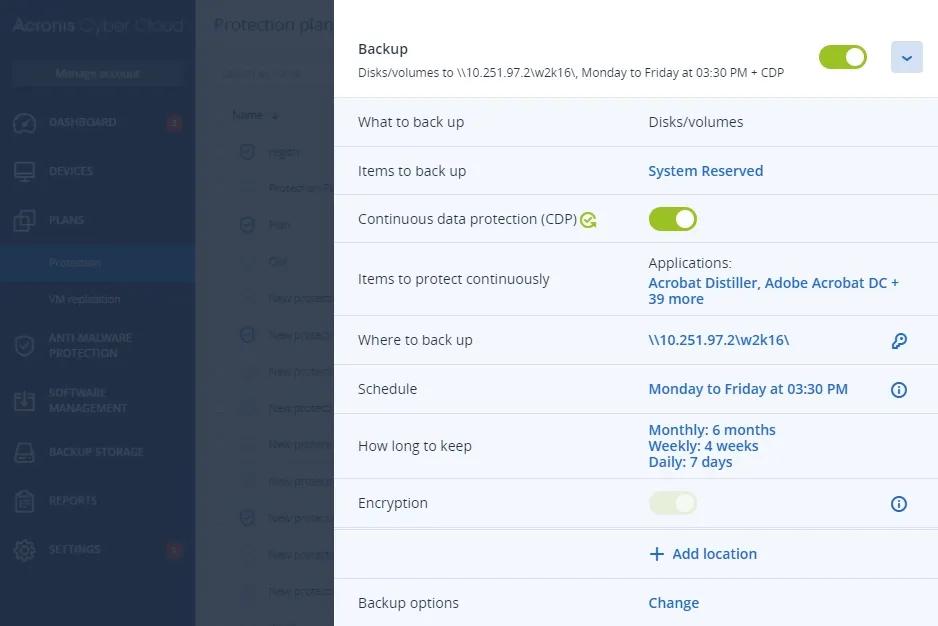
Continuous data backup and protection
By adding Advanced Backup to Acronis Cyber Protect Cloud, you can eliminate downtime while simultaneously protecting from advanced threats. Continuous data protection captures and backs up changes made in real-time from business-critical applications so no data is lost.

RAPIDLY RECOVER FROM CYBERATTACKS AND OTHER UNPLANNED OUTAGES
Acronis’ Advanced Disaster Recovery enables you to restore operations in a few clicks, without any upfront investments, so you can rapidly recover workloads or services in the event of ransomware, hardware failure, and any other disruption.


INTERCEPT MODERN EMAIL ATTACKS WITHIN SECONDS
Block email threats, including spam, phishing, business email compromise (BEC), account takeover (ATO), malware, advanced persistent threats (APTs), and zero-days before they reach your mailboxes. Leverage this next-generation, cloud-based email security solution for holistic protection.

Phishing
Phishing attacks leverage social engineering to deceive their target and gain access to sensitive information by employing files, URLs, and text-based techniques posing as legitimate sources. Advanced Email Security such as Anti-evasion, URL reputation, Image recognition engine, and Threat intelligence.
Malware and ransomware
Malware – including viruses, ransomware, spyware, worms, and Trojans - is most commonly delivered via malicious payloads – files and URLs. Thousands of new malware variants appear each day. Advanced Email Security such as Anti-evasion, Threat intelligence, Anti-phishing filters, Antivirus engines, and Next-generation dynamic engine.


PREVENT LEAKAGE OF SENSITIVE DATA
For years, organizations have struggled to prevent data exfiltration due to internal risks or external attacks, leading to embarrassing headlines, loss of business, and regulatory fines. Advanced DLP empowers you to prevent data leaks from endpoints — without requiring months to deploy, teams to maintain, or a Ph.D. in privacy law to understand.

Malware and ransomware
Minimize risks of data leakage and exfiltration by detecting and preventing sensitive information from being transferred to unauthorized parties. Simplify compliance reporting and increase visibility of DLP performance with information-rich widgets. Ensure that DLP policies are aligned with each business specifics.


SECURE COLLABORATION SERVICES WITH DATA AUTHENTICITY
The Advanced File Sync integrated secure file-sharing capabilities with fully remote notarization, verification, and online signing. Ensure data authenticity and reduce fraud by layering advanced features on top of the essential. Maximize productivity with collaboration by enabling them to easily share data and files with colleagues, customers, and partners. Mitigate security risks with controlled access, custom permissions, eSigning, and file notarization.

Provide confidence that business data is authentic
Notarize files of any format and type, generating a certificate that provides irrefutable proof that the file was notarized at a specific time. With blockchain-based data notarization, you will have a public and immutable way to prove that the data is original and unaltered.

SIMPLIFY PROTECTION MANAGEMENT AND PATCH AUTOMATION
Spend less time juggling solutions and more time focusing on managing, monitoring and protecting your clients’ data, applications and systems. Adding Advanced Management to Acronis Cyber Protect Cloud enables you to automate your daily tasks and proactively mitigate existing vulnerabilities with patching of open security gaps.


